Edit 04/01/18: Ethereum Wallet Cracking Pt 2. – GPU vs CPU can be found here
hashcat v3.6.0 was released yesterday and one of the newly supported hashes was Ethereum wallets (Go Ethereum (Geth), Mist and MyEtherWallet variants). This guide will show how a MyEtherWallet JSON keystore file is broken down, how it’s mapped to a hashcat compatible format, and finally an example crack.
First let’s get our wallet. That’s as easy as going to MyEtherWallet, entering a password, clicking generate and downloading it. MyEtherWallet suggests you “enter a strong password (at least 9 characters)”. Firstly this isn’t a suggestion it won’t let you generate your wallet unless your it’s at least 9 characters. Secondly, I wouldn’t say 9 characters is particularly strong, but that’s an argument for another day. If you don’t set a wallet name, a default is provided (as ours is) which comprises of the UTC time/date generated, followed by your new Ethereum wallet address.
Our wallet’s password is P@ssw0rd1! and the generated keystore file can be found below which is coloured to show how it’s mapped to the hashcat compatible format.
UTC–2017-06-10T11-51-33.675Z–f418f8185f2c1163ae953bf778acc6877b9bc203
{“version”:3,”id”:”5cf4711d-3f69-4636-89d0-b304a7e23b75″,
“address”:”f418f8185f2c1163ae953bf778acc6877b9bc203″,
“Crypto”:{“ciphertext”:”7f5c865554d67604394ae54d7a4f9735bdb85c90e606a672d18add1d167d793b“,
“cipherparams”:{“iv”:”ae4e8c9c2ac201d6c2baa58ff670fd39″},
“cipher”:”aes-128-ctr”,
“kdf”:”scrypt”,
“kdfparams”:{“dklen”:32,”salt”:”437964c9bd1b5f63bde56560808c894792f8f670694590b776e22381e32dd
33b“,”n”:1024,”r”:8,”p”:1},
“mac”:”96f2a849321cc04cb6c0fcee1bd4b195ca681ca28064dc45000f02e47230c5b6“}}
hashcat Format
$ethereum$s*1024*8*1*437964c9bd1b5f63bde56560808c894792f8f670694590b776e22381
e32dd33b*7f5c865554d67604394ae54d7a4f9735bdb85c90e606a672d18add1d167d793b*96f
2a849321cc04cb6c0fcee1bd4b195ca681ca28064dc45000f02e47230c5b6
So from the above we can derive the following hashcat structure…
$ethereum$s*n*r*p*salt*mac*ciphertext
EDIT (07/05/19): Meant to update this for a while, $ethereum$s*n*r*p*salt*ciphertext*mac (as shown in above example) is the correct format.
EDIT (17/07/17): Despite documentation showing the above structure due to transitions between ethereum2john versions, hashcat will accept both $ethereum$s*n*r*p*salt*ciphertext*mac (as shown in this example) and $ethereum$s*n*r*p*salt*mac*ciphertext formats.
…where s references scrypt variant in this instance. The letter p could also be found which indicates it’s a PBKDF2 variant. Fortunately ethereum2john.py makes the hashcat prep easy (you heard me right, ethereum2john for hashcat prep… ether2hashcat was superseded by it) by just pointing it at the wallet as shown below.
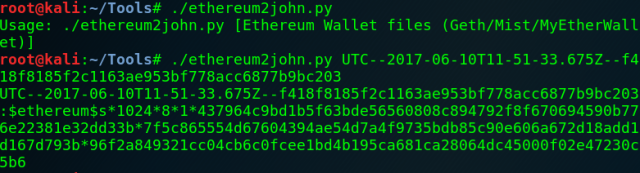
Now we’ve got the hash we can pass it over to hashcat. As we’ve got an scrypt based hash a quick lookup shows the required hashcat mode is 15700.
hashcat64.exe -m15700 $ethereum$s*1024*8*1*437964c9bd1b5f63bde56560808c894792f8f670694590b776e22381e32dd33b*7f5c865554d67604394ae54d7a4f9735bdb85c90e606a672d18add1d167d793b*96f2a849321cc04cb6c0fcee1bd4b195ca681ca28064dc45000f02e47230c5b6 b:\Dictionaries\rockyou.txt --status --status-timer=5 -w3 -r rules\hob064.rule
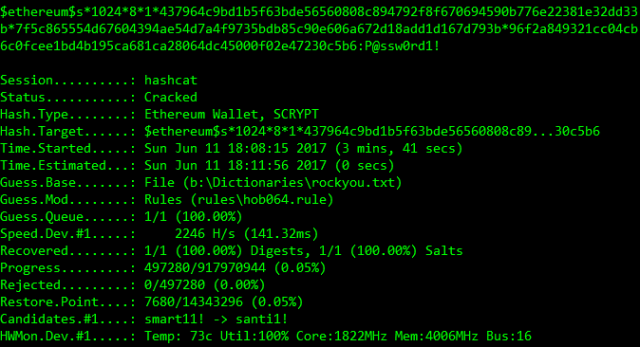
3 mins 41 secs @ circa 2200 H/s, job done. FYI this laptop has a mobile GTX 1060.
A couple of general password cracking points to note here…
- The password – P@ssw0rd1! isn’t in the standard rockyou dictionary so assuming this dictionary is being used (and commonly is), a non-rule based attack wouldn’t have cracked it.
- The rule – They’re important, as I literally just said above 😀 . Algorithm complexity should always be a factor when choosing one. For example, I throw bigger rule sets against fast hashes (e.g. MD5, NTLM) as the speed you’ll crack at will exhaust the larger rule set quicker. As Ethereum scrypt hashes are heinously slow, I’ll throw smaller, more efficient rule sets (relative to size) against it first.
The hob064 rule set used above is very efficient and good first choice when attacking complex algorithms. I’ve already written about hashcat rule efficiency on NotSoSecure’s blog (where you’ll note the most efficient rule tested was hob064). When attacking fast hashes I tend to use my own larger custo m rule, derived from a number of high performing rules against a large hash set. This custom rule was created from the testing noted in the above linked blog, and can be found here if you want to give it a go… although you’ll be waiting a while if you throw it against an Ethereum wallet with a good password!
Edit 04/01/18: A follow up covering why hashcat can crash on Ethereum wallets and GPU/CPU differences can be found in part 2.
Does not work for me: always finishes with Exhausted status.
LikeLike
Is your rockyou dictionary and hob064 rule modified in any way? The default dictionary rule will crack the example password used above. If you’re still having trouble paste your hashcat command here 🙂
LikeLike
having some trouble. exhaust in one try: ./hashcat -m 15700 hash.txt /Users/ry/github.com/hashcat/Dict/rockyou.txt –status –status-timer=5 -w3 -r /Users/ry/github.com/hashcat/rules/d3adhob0.rule
LikeLike
I don’t know exactly what’s in your hash.txt, but make sure it’s formatted exactly how the post shows. Replace your hash.txt parameter with
$ethereum$s*1024*8*1*437964c9bd1b5f63bde56560808c894792f8f670694590b776e22381e32dd33b*7f5c865554d67604394ae54d7a4f9735bdb85c90e606a672d18add1d167d793b*96f2a849321cc04cb6c0fcee1bd4b195ca681ca28064dc45000f02e47230c5b6
Also, the example uses hob064, not d3adhob0 as you were.
LikeLiked by 1 person
Thanks for this nice tutorial. Here u are using the mobile GTX 1060 and have 2200H/s on a laptop and i’m using a desktop with a NVIDIA GeForce 2070 Super and only getting +/- 200H/s. My card is compared with yours better and should do much more then the current 200H/s. Is there something i’m doing wrong? I can find the problem and searching for it all day. If i use a small list with the word “password” it finds it in seconds, but using “rockyou.txt” after 40′ and counting, i’m still waiting for the result.
LikeLike
{“address”:”e5073c7e598a15ff6902f3d691e716be0dee8db1″,”crypto”:{“cipher”:”aes-128-ctr”,”ciphertext”:”602323b0d50e5f12f1ad61a271ab9e12629572d7c3d6ea3950b24f991d4ebdcb”,”cipherparams”:{“iv”:”4cfc5544fff57448955246170ba0db31″},”kdf”:”scrypt”,”kdfparams”:{“dklen”:32,”n”:4096,”p”:6,”r”:8,”salt”:”3384860f3e361300e07aa481a4157b48721411557192b486fa7d73d7669ef8f8″},”mac”:”9ef3b17d5f6aa97f1903bd93fa286d0341bb4dc59090065f024857cb216d38dc”},”id”:”00b6a2d8-7a4a-4252-842d-80799f4e9f7a”,”version”:3}
LikeLike
Hi there. I’m not sure what you’re asking by pasting that? Hashcat will accept that, but you’ll need to reorder the parameters into the order as shown in the post for ethereum2john to accept it. Doing so will provide the following hashcat format:
$ethereum$s*4096*8*6*3384860f3e361300e07aa481a4157b487214
11557192b486fa7d73d7669ef8f8*602323b0d50e5f12f1ad61a271ab
9e12629572d7c3d6ea3950b24f991d4ebdcb*9ef3b17d5f6aa97f1903
bd93fa286d0341bb4dc59090065f024857cb216d38dc
Also, your wallet likely won’t crack on GPU’s (I couldn’t get it running) because of the memory requirement from your kdfparams. Trying it on GPU’s will liekly hang/crash the system. CPU cracking will work fine but the speed will be really slow (I got 115 h/s on yours).
When you run hashcat it lists the devices (CPU, GPU etc) that are present. If your CPU is device 1 for example, run hashcat with your desired options but add -D 1 and it’ll work fine.
LikeLike
Hey, I tried the whole thing. ethereum2john.py give me the correct hash but when I run it when hashcat, I have the following error:
> Hash ‘*n*r*p*salt*cypertext*salt’: Line-length exception
(vars are obiously obfuscated)
My N is huge, like 262144. What can I do?
LikeLike
You’ve got a couple of problems here, one of which I’ve outlined in the previous question.
1)
Firstly, if hashcat reports a Line-length exception, it typically means that either you’ve assigned the wrong hash type (in this case possibly -m15600 instead of -m15700 ?), or that the hash is incorrectly formatted (more likely). Please check that your string is *exactly* formatted as shown in my example. I haven’t tested ethereum2john’s error handling but ensure that your salt, mac and ciphertext are all correct.
Both $ethereum$s*n*r*p*salt*ciphertext*mac (as shown in my example) and $ethereum$s*n*r*p*salt*mac*ciphertext formats will work.
2)
Yes, your high scrypt settings will mean that a GPU won’t be able to crack due to the memory requirement. You’ll need to solve your line length exception issue anyway, but after you’ve done that, you’ll only be able to attempt to crack using your CPU. Run hashcat with -b to identify which device your CPU is, let’s say it’s device #1… Then when attempting your Ethereum crack, append -D 1 to the end of them command and it’ll skip your GPU and perform a CPU crack which should work fine. It won’t crack quickly though!
LikeLike
What is the determining factor of high scrypt settings? Why do n values vary so much between wallets? If you have some kind of general idea of the length of a password and the makeup of such a password, for example 3 words and a set of numbers in the middle would you be better off doing a mask attack, higher success rate? Thanks 🙂
LikeLike
As far as I know these settings differ between various implementations of scrypt. For example, in Ethereum, the scrypt defaults are n:262144, r:1, p:8 but different wallets may implement different factors.
This post does a good job of describing what n, p and r are in scrypt. The tl;dr is that if n is very high, there’s a good chance you won’t be able to GPU crack it because you won’t have the RAM.
If you have an idea as to the password’s structure, then you’re already in a much better position to crack it. I’d approach it the same way I would any hashing algorithm.
E.g. if I knew there were numbers at either the start or end of a ‘3 word’ wordlist, I’d create the 3-word wordlist (This post shows you how to quickly create a list using hashcat’s combinator tool) and use it with a mask file containing your numbers (?d, ?d?d, ?d?d?d etc), running it once for each end. If we assume you’ll be CPU cracking due to the RAM problem, examples would be:
-a6 -D1 -m15700 hashfile 3wordlist numbers.mask
followed by
-a7 -D1 -m15700 hashfile numbers.mask 3wordlist
LikeLike
Are there any GPUs or hardware settings that could handle N being 262144? Thank you!!
LikeLike
There’s only one as far as I know, but it’ll cost $7000
https://www.pcgamer.com/amd-radeon-pro-ssg-pairs-vega-with-2tb-of-memory/
LikeLike
Sorry hadn’t finished reading through the comments, so the answer to my previous question is that I would need 2 GPUs with 160GB of RAM each?
LikeLike
Also, could you tell me how you came up with those numbers? Thank you
LikeLike
Seems I misread the number of SMs a GTX 1060 has as 20 instead of 10 when replying to the original comment, so a 1060 wouldn’t require 160GB of RAM, it would need 80GB. Either way, the formula is in the post, and it’s still GPU uncrackable without that $7k card. GTX 1060 calculation is below.
(8 * 128) * 262,144 = 268,435,456 bytes = 256 MB
32 * 10 = 320 parallel computations required (1060 has 10 compute units)
256 MB * 320 = 81,920 MB = 80 GB RAM required per GPU
LikeLike
Realistically N at 262144 rules out GPU cracking all together unless you get the $7k card. The 160 GB number will vary though depending on the graphics card. https://www.techpowerup.com/gpudb/2839/geforce-gtx-1080 . In the case of a GTX 1080 it’s 160 GB.
LikeLike
help
LikeLike
I’m afraid you’re going to have to be a little more specific!
LikeLike
I’m sorry, sorry, that was a test because I wrote a bunch of posts and my antivirus blocks your site constantly, I have a problem with brute on the video card, help me please, the problem is that if without -D 1 my pc hangs completely and helps only the reset button, in your version $ ethereum $ s * 1024 * 8 * 1 and everything is fine, but in my versionnt 262144 * 8 * 1 please tell me whether it is possible to somehow run brute using a video card 262144 * 8 * 1 and PC did not hang? on 1024 * 8 * 1 does not hang, until the block on -D 1 11H/s on CPU i7 3770
My pc –CPU i7 3370 / RAM 16gb / 2*gtx1060 6gb / ssd+hdd
my hash:
????? Hashcat64.exe -m15700 -D 1 $ ethereum $ s * 262144 * 8 * 1 * 5af5c013e170e5506a972098ac631d1ea896813db05beb8e0c64f277bc12e61e * bc46586dc16add0cc22bf666e075fb064df73ec281ecffc626fda4288d56ea50 * bd3f8d428b655cb2a2ea2c54d6a7a6443e79d699edda6e31657fe63825e3868b 5e7Vqty l l l l l –status –status-timer = 5 -w3 – status –status-timer = 5 -w3
I heard you can somehow reduce the load on the video card and this PC will not hang, so that not 100% of it brutila
Yes, and there is a pre-correct password and with it seems to have once deduced funds, but this is not certain, maybe this is a bug if so how to solve it?
LikeLike
Your system will always hang as your kdfparams (262144*8*1) result in a large RAM requirement (meaning you can only CPU crack). I won’t go into the maths, but with those settings, a *single* GTX 1060 will need 160GB RAM (which of course you don’t have) to work on that hash. In other words, when you start hashcat, it’s trying to use 320GB RAM over both your cards and will bomb out. So unfortunately you’re stuck with -D1 or whatever number your CPU is listed as.
Regarding your GPU load reduction, you’re probably referring to Time Memory Trade Off (TMTO), but you’ll barely get 1h/s going down that route so I honestly wouldn’t bother. Higher scrypt settings make it an algorithm that can be very resilient to GPU cracking.
LikeLiked by 1 person
thanks, very detailed explained, maybe you know some more ways to find out the password? but then I do not know what to do with this problem, because even if 12 characters to brute at a rate of 1 milliard per second, it turns out 10 years)
LikeLike
can reduce the load on the processor with brute, but lose 1 hash, but I can freely use the PC, do not tell me? your article is like salvation, thanks again
LikeLike
There isn’t another viable way that I’m aware of to crack high scrypt settings like those with any speed. You’re only choice is CPU cracking which will be slow. I typically wouldn’t advise brute-forcing the entire keyspace of a password because as you said, as the length of the password increases, the time required will become years very quickly. The practical way to crack passwords is by dictionary attacks, so unless the password to your wallet is something that would commonly be found in a wordlist, it’s probably not worth your time attempting to break it.
Removing the -w3 will tell hashcat to use the “default” workload profile, which will make the system respond more. Using a -w3 will slow down responsiveness and -w4 will make it almost unusable.
LikeLiked by 1 person
I’m flattered if I can still crack the password by all means, I’ll write to you and thank you, and even such a question, maybe somehow you can find out how many characters in the password on the hash? and could not explain how to brute the mask correctly? For example :
– [Built-in Charsets] –
? | | Charset
=== + =========
l | abcdefghijklmnopqrstuvwxyz
u | ABCDEFGHIJKLMNOPQRSTUVWXYZ
d | 0123456789
h | 0123456789abcdef
H | 0123456789ABCDEF
s | ! “# $% & ‘() * +, -. / :; ? @ [\] ^ _` {|} ~
a | ? l? u? d? s
b | 0x00 – 0hff
my password for example – 5e7Vqyp2Qrpd
how do I properly write a mask for the last 3 characters so that she croaks both small and large and numbers at once?
5e7Vqyp2Q?luhHs?luhHs?luhHs Probably like this?
LikeLike
You’ll never be able to work out how many characters the plain text password is from the hash. Hashing algorithms take an arbitrary length input and produce a fixed length output.
Using your example password you could use a mask attack to try and crack it (but it still might take some time at CPU cracking speeds). If you want the last 3 characters masks you’d use 3 lowercase letters (assuming you knew the password), so you’d provide hashcat the following:
Hashcat -a3 -m15700 -D1 hash 5e7Vqyp2Q?l?l?l
If you didn’t know the last 3 characters and wanted to try just mixed-alpha you’d need a custom char set containing mixed alpha:
Hashcat -a3 -D1 -m15700 -1 ?l?u hash 5e7Vqyp2Q?1?1?1
And if you wanted to try all combinations for the last 3 places just use the first example but replace ?l for ?a
LikeLiked by 1 person
ok, i dont know 3 last simbols i write this – 5e7Vqyp2Q?a?a?a yes? if i can last 3 simbols only big-small-number how write mask?
LikeLike
Yes. In that example the last 3 characters will be tested of mixed-alphanumeric and symbols. If you only wanted mixed alpha-numeric without symbols then you would create a custom character set similar to last response that assigns lower(?l), upper (?u) and numbers (?d) into a single character set:
Hashcat -a3 -D1 -m15700 -1 ?l?u?d hash 5e7Vqyp2Q?1?1?1
LikeLiked by 1 person
if GTX 1080 will need 160GB RAM (which of course you don’t have) to work on that hash but if i buy 20×1080 8gb in one farm=160gb? program start in vedeocard?
LikeLike
No this wouldn’t work either. When the maths is worked out for a GTX 1080 the RAM the requirement becomes 320GB per card. You could have 100x GTX 1080s and it still wouldn’t work because the RAM requirement is per GPU. Your card will always only have 8GB
LikeLiked by 1 person
and this card can brutforce, I’m more interested in the speed of the similar purse here, https://www.pcgamer.com/amd-radeon-pro-ssg-pairs-vega-with-2tb-of-memory/
{“address”:”??????????”, “Crypto”:{“cipher”:”aes-128-ctr”,”ciphertext”:”???????????”,”cipherparams “:{“iv”:”??????????”},”kdf”:”scrypt”,”kdfparams”:{“dklen”:32,”n”:262144,”p”:1,”r”:8,”salt”:”????????????”},
“mac”:”??????????????”},”id”:”17de2532-b776-457f-987f-?????????”,”version”:3}
hashcat64.exe -a3 -D1 -m15700 $ethereum$s*n*r*p*salt*ciphertext*mac masks.hcmask –status –status-timer=5 –force
sank
LikeLike
Not sure what you’re asking, I don’t have any idea what speeds the 2TB GPU would get I’m afraid. Raw brute forcing the hash with or without masks won’t give you any decent speeds via CPU, and until someone’s able to benchmark that new card against an scrypt wallet we won’t be in any better position unfortunately.
LikeLiked by 1 person
Hey there, so this is going to sound pretty silly but I was hoping to crack my personal MyEtherWallet password. I set it up some days ago and forgot the password (yeah, i know). I tried using the pyethrecover tool (https://github.com/ryepdx/pyethrecover) since I’ve still got my keystore file on hand I figured i’ll supply a light dictionary and give it a go. Needless to say, I found it really laborious and it didn’t help in cracking my password.
Can I use hashcat locally on my computer to try out different password combinations so that it works with that python script above? Any help would be greatly appreciated.
LikeLike
Hi, I haven’t seen that script before and although i’m sure it works fine, you may find better speeds using hashcat locally as it will better utilise your GPU. If you’ve got a JSON file like shown in the post then you should be able to identify and match the various elements required to pass it to hashcat. The post details what you need and the format hashcat expects.
Wordlists like rockyou are pretty standard, however if you’ve got even a hint of what you thought your password was I would definitely add it into the start of the dictionary you use (or any passwords you think it might be). By giving hashcat some basic rules you may get lucky. Please remember that eth wallets use scrypt which is a really slow algorithm, so don’t expect very fast speeds.
LikeLiked by 1 person
Hey thanks so much for your reply, and after learning some more about hashcat and re-reading this blog I’m convinced it has everything that I need to get myself started.
I’m using v4.0.1 of hashcat on OS X but I keep getting hammered by the Line-length exceeded error. Here’s the output of the ethereum2john.py:
$ethereum$s*1024*8*1*5352338077a20d8078b96b4d9c53bdcf0a34a7fa33b760911ab7e17e0a2bf9ec*29ec32b07c8a1e8aefad249df3545cce9c921d8f5160e17b767914f33549ee3a*020b912e14a6cf2e8d5e632bf1f3dad4722f3d25625820d0cda5fc28d4637d33
and the final command on my terminal ends up looking like this:
hashcat -m15700 $ethereum$s*1024*8*1*5352338077a20d8078b96b4d9c53bdcf0a34a7fa33b760911ab7e17e0a2bf9ec*29ec32b07c8a1e8aefad249df3545cce9c921d8f5160e17b767914f33549ee3a*020b912e14a6cf2e8d5e632bf1f3dad4722f3d25625820d0cda5fc28d4637d33 rockyou.txt –status –status-timer=5 -w3 -r hob064.rule
hashcat (v4.0.1) starting…
OpenCL Platform #1: Apple
=========================
* Device #1: Intel(R) Core(TM) i5-7360U CPU @ 2.30GHz, skipped.
* Device #2: Intel(R) Iris(TM) Plus Graphics 640, 384/1536 MB allocatable, 48MCU
Hash ‘*1024*8*1*5352338077a20d8078b96b4d9c53bdcf0a34a7fa33b760911ab7e17e0a2bf9ec*29ec32b07c8a1e8aefad249df3545cce9c921d8f5160e17b767914f33549ee3a*020b912e14a6cf2e8d5e632bf1f3dad4722f3d25625820d0cda5fc28d4637d33’: Line-length exception
No hashes loaded.
Any ideas on how to proceed?
LikeLiked by 1 person
I tried your command and it worked without issue.
Session……….: hashcat
Status………..: Running
Hash.Type……..: Ethereum Wallet, SCRYPT
Hash.Target……: $ethereum$s*1024*8*1*5352338077a20d8078b96b4d9c53bd…637d33
Time.Started…..: Sun Dec 17 10:28:43 2017 (4 secs)
Time.Estimated…: Thu Mar 22 12:00:57 2018 (95 days, 1 hour)
Guess.Base…….: File (b:\Dictionaries\rockyou.txt)
Guess.Mod……..: Rules (rules\hob064.rule)
Guess.Queue……: 1/1 (100.00%)
Speed.Dev.#2…..: 112 H/s (87.08ms)
Recovered……..: 0/1 (0.00%) Digests, 0/1 (0.00%) Salts
Progress………: 520/918040576 (0.00%)
Rejected………: 0/520 (0.00%)
Restore.Point….: 0/14344384 (0.00%)
Candidates.#2….: 123456 -> abc123
HWMon.Dev.#2…..: Temp: 43c Util: 99% Core:1873MHz Mem:3802MHz Bus:16
Line length exceptions are typically one/both of two things: incorrect mode or incorrect hash length received (i.e. typo/wrong format). Your mode is correct so it must be a character(s) in your string. Check that the asterisk delimiters are the correct character for example.
As your error started with ‘*1024 it suggests that the $ethereum$s portion of the command wasn’t entered at the start (removing it from the start duplicates your exact error).
If there was a typo further down the string you would have received “Salt-length exception. No hashes loaded.”
Drop the status, rules etc, go over it carefully and make sure nothing’s incorrect first, then build it up.
Also fyi, since v4 the core code has been re-written and you can generally sacrifice higher max password lengths for speed by adding -O
LikeLike
Turns out that my shell was interfering with things; I merely took the output of the python file and saved it in a text file (hash.txt). This let me get to the next step!
hashcat -m 15700 –force hash.txt rockyou.txt –status –status-timer=5 -w3 -r hob064.rule
You’ll notice that I’ve included the “–force” flag because without it I get this message:
* Device #2: Skipping unstable hash-mode 15700 for this device.
You can use –force to override, but do not report related errors.
I’m guessing the device drivers are screwed up? I guess i deserve that for installing this via brew.
LikeLike
Possibly yes, however I won’t lie I’m not 100% what that could be. Google shows someone else who’s had that with -m15700 however their GPU is different, https://hashcat.net/forum/showthread.php?mode=linear&tid=7108&pid=38104
Best thing to do is check to see if the error prevents it from finding a known password. So download a test wallet from MyEtherWallet or whatever, give it a password, check you get the same error without force, then run it with –force and use a dictionary containing just your password. If it cracks it I’d continue with your first wallet under the assumption that hashcat will crack it (if the pw is in your dictionary of course 😉 ).
LikeLike
hello! i need help brute passvord! my hash
$ethereum
$s*262144*8*1*359207e61210d962a9da470667e4c25f9fd993c09a099d392ae0e4441d6b0069*b8d7a34b70be8cdbfda1b230086e4664f9c894d47d3ee6ea7beec943437e4422*3ddaf1eca967e61a5e2a740ebe201b5638587fb2b838dfbd4fbad076f9e7f6ca
LikeLike
I removed the list of potential passwords you provided as there was an email address present and I wouldn’t recommend exposing potential passwords publicly.
You will need to CPU crack that so run your hashcat command and specify your CPU with -D
You’ll see something like this when you start
OpenCL Platform #1: Intel(R) Corporation
* Device #1: Intel(R) Core(TM) i7-7700HQ CPU @ 2.80GHz, skipped.
OpenCL Platform #2: NVIDIA Corporation
* Device #2: GeForce GTX 1060, 1536/6144 MB allocatable, 10MCU
In this case my CPU is device 1 so I would append -D 1 to the end of my command
LikeLike
At me as touches.
Please tell me how to do file-by-dictionary search. for example I have the words 123456789 234567890 artem artemartem@gmail.com! @ 433
how do I search a bunch of words, at first 123456789 234567890 then 123456789 artem
Further when such pairs of words are interrupted.blowing already move 3 words. blowing already move 4 words. blowing already move 5 words. then in each pair at the end of the brute 3 symbols 433! @
LikeLike
tell me which team to search for crunch kali linux and then brute! @ 433
LikeLike
Sorry, don’t really understand what you’re talking about here.
If you want to do a dictionary search with your guesses, put them into a file then run a normal hashcat session:
hashcat
If you want to add specific characters, e.g. 433! to the end of your guesses, you need an -a6 hybrid attack:
hashcat -a6 433!
If you want to add any 3 numbers + symbol combination you’d use
hashcat -a6 ?d?d?d?s
You can read how to create masks here, https://hashcat.net/wiki/doku.php?id=mask_attack
Here’s a guide to using crunch, https://null-byte.wonderhowto.com/how-to/hack-like-pro-crack-passwords-part-4-creating-custom-wordlist-with-crunch-0156817/
LikeLiked by 1 person
Pingback: Ethereum Wallet Cracking Pt. 2 – GPU vs CPU | Stealthsploit
Hi. I’m trying to bruteforce my passcode. All I know is that my password is 31 characters long and complete random mixture of upper and lower case letters, digits and symbols like “[/=-$@” and so on… Is this even possible to achieve? What settings to use? I’m getting an integer overflow warning on my mask. Thank you.
PS: My command looks like this: ./hashcat -a3 -D1 -m15700 -1 ?a hashes.txt ?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l?l
LikeLike
You won’t be able to brute force that length as the keyspace is way too big. On a 64-bit OS you’re limited to a keyspace that can be handled in 64-bits.
2^64 = 18,446,744,073,709,551,616 (available keyspace on 64-bit)
Keyspace of password = Char set ^ password length, so in your case …
95^31 = 2.0390682574579068859408986143361e+61 (keyspace of 31 char password using full 95 ASCII set, i.e. mixed alpha-num with symbols)
As 95^31 > 2^64, hashcat won’t handle it and to be honest that’s too much for modern hardware all together.
On top of this, cracking scrypt is slow enough already, you’d never crack a 31 char password with it. The only possibility would be is if you knew the first 26 characters, for example, and then applied a mask for the last 5. I’m afraid you’re stuck with good old dictionary attacks (obviously you’d need to generate a dictionary containing 31 length candidates only)
LikeLike
Hello and thanks for this great and useful article !!
Had the same problem as many here, Line-length exception No hashes loaded.
Solved it by putting my hash in a text file and the command worked… same hash, no problem.
./hashcat -m 15700 hash11.txt rockyou.txt –status –status-timer=5 -w3 -r hob064.rule -D1 –force
If somebody know a way to feed a script with a list of different password and extract a list of rules for them it will be a great help. Best to you all.
LikeLike
Guess this page is pretty explanatory to create your own set of rules.
LikeLike
If you mean, create a list of possible candidates based on a custom dictionary you provide, then hashcat can do that with –stdout
hashcat passwordlist -r rule –stdout
The above will mangle your passwords for you, then just output it to a file.
LikeLike
thanks very useful. feeling more at ease with tweaking and setting rules now.
LikeLike
Hello again. And thanks for your tips, even if I didn’t crack my passwords yet, I would have learn how to play with hash cat and that’s great !! I would like to write an article based on your post to help the French community who are locked out of their wallet. Do you mind ? and would you like to be linked as source ? might cause an avalanche of stupid questions written in poor English LOL
All the best
LikeLike
Happy for you to write something based on this and yes would appreciate it if you could back to this post. Email me the link once it’s up so I can point people there in the future if needed. Thanks.
LikeLike
Hi Stealthsploit
Do you happen to crack wallets for a fee?
I currently have my JSON file and also have a pretty good idea of what my password is, but have no idea how to do a brute force or anything of that nature.
Regards
LikeLike
Hey, I wouldn’t ask for a fee. If you have a good idea about what it could be, I’d try a mask attack. Check my replies on the 10th/11th November last year on the first post about this, might be what you need.
If you’re still stuck on mask attacks, DM me on twitter or email with more details.
LikeLike
I am not tech savvy and was hoping someone could help me. I bought Crypteruim Tokens which we where told to move to a My Ether Wallet. I created one 0x64BAdB43514a92C0DBE8d54Fa5965C3f87e701AA and move my tokens to the account. A day later I was hacked and my tokens where first moved to : 0xff714f17dcf5d9db0cc3b814e415ace61f6cdb09 and than from this account to
0xD31B1bEe0C9f42Cb47406D52a796d8a26C5CF802. All I want is my tokens back. Is there someone that can help My Ether Wallet help centre has done nothing to assist in this. I had 120.3546436767 Crypertium Tokens. I am very sad that this has happened. If you can help please email me with any additional information you need and I have created a new My Ether Wallet account as I am scared that it is easy to hack my previous one. PLEASE HELP! I think it is terrible that people can take what isn’t theirs this person has done this to lots of people you can see it if you search the wallets and not just tokens but coins and other tokens.
LikeLike
@RecoveryETH telegram
LikeLike
Thank you for the post, very interesting information.
LikeLike
Hello bro, i can’t understand how you get 2246 h/s speed with 1060 gpu
my rig of 7 x 1080ti make only 2 h/s, on hashcat forum guys told that SCRYPT is very bad for gpu.
LikeLike
Scrypt is very GPU resistant that’s correct, you are better off CPU cracking. The example shown in the post is a couple of years old now and has weaker scrypt params if you downloaded a wallet recently, so if you’re trying to crack a recent wallet you won’t get the same speeds.
LikeLike
Hi, I was using eth wallet in my cell but crash it now i have a json file which i rescue from phone, i tried the script but it wont gave me the hash. it gaves wallet gasprice nonce blockchain ID etc.. I remember 24 keywords from 26 just 2 missing… how can i resolve it ?
LikeLike